Red Stealer Write-up
:الحمد لله والصلاة والسلام على رسول الله وعلى آله وصحبه أما بعد
Scenario:
Tools:
Questions:
1. Categorizing malware allows for a quicker and easier understanding of the malware, aiding in understanding its distinct behaviors and attack vectors. What’s the identified malware’s category?

2. Clear identification of the malware file name facilitates better communication among the SOC team. What’s the file name associated with this malware?

3. Knowing the exact time the malware was first seen can help prioritize actions. If the malware is newly detected, it may warrant more urgent containment and eradication efforts compared to older, well-known threats. Can you provide the UTC timestamp of first submission of this malware on VirusTotal?

4. Understanding the techniques used by malware helps in strategic security planning. What is the MITRE ATT&CK technique ID for the malware’s data collection from the system before exfiltration?

5. Following execution, what domain name resolution is performed by the malware?
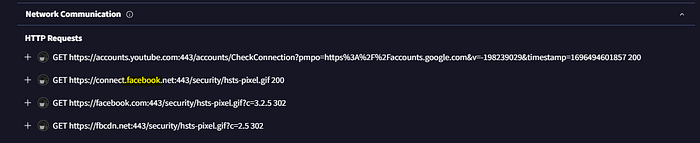
6. Once the malicious IP addresses are identified, network security devices such as firewalls can be configured to block traffic to and from these addresses. Can you provide the IP address and destination port the malware communicates with?

7. YARA rules are designed to identify specific malware patterns and behaviors. What’s the name of the YARA rule created by “Varp0s” that detects the identified malware?

8. Understanding which malware families are targeting the organization helps in strategic security planning for the future and prioritizing resources based on the threat. Can you provide the different malware alias associated with the malicious IP address?

9. By identifying the malware’s imported DLLs, we can configure security tools to monitor for the loading or unusual usage of these specific DLLs. Can you provide the DLL utilized by the malware for privilege escalation?

You Can Find me Here!
Last updated