BlueSky Ransomware Write-up
:الحمد لله والصلاة والسلام على رسول الله وعلى آله وصحبه أما بعد
Scenario:
Tools:
Questions:
1. Knowing the source IP of the attack allows security teams to respond to potential threats quickly. Can you identify the source IP responsible for potential port scanning activity?

2. During the investigation, it’s essential to determine the account targeted by the attacker. Can you identify the targeted account username?

3. We need to determine if the attacker succeeded in gaining access. Can you provide the correct password discovered by the attacker?

4. Attackers often change some settings to facilitate lateral movement within a network. What setting did the attacker enable to control the target host further and execute further commands?
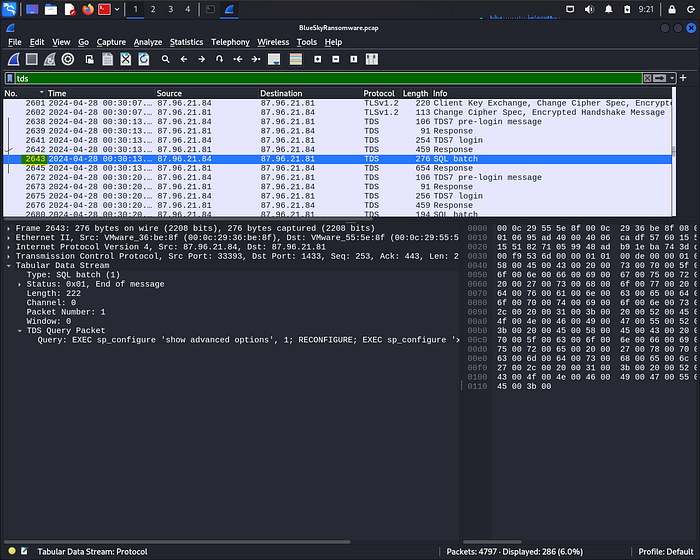
5. Process injection is often used by attackers to escalate privileges within a system. What process did the attacker inject the C2 into to gain administrative privileges?
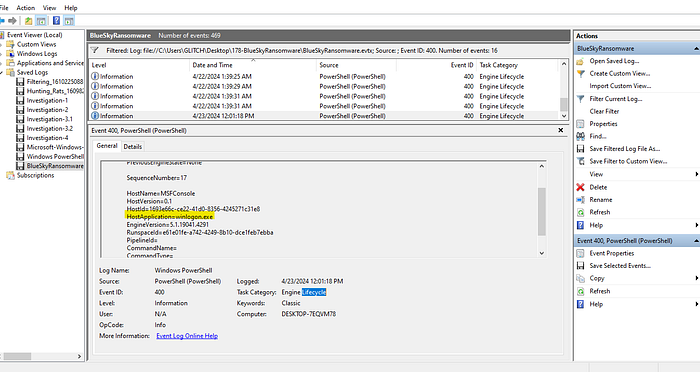
6. Following privilege escalation, the attacker attempted to download a file. Can you identify the URL of this file downloaded?

7. Understanding which group Security Identifier (SID) the malicious script checks to verify the current user’s privileges can provide insights into the attacker’s intentions. Can you provide the specific Group SID that is being checked?

8. Windows Defender plays a critical role in defending against cyber threats. If an attacker disables it, the system becomes more vulnerable to further attacks. What are the registry keys used by the attacker to disable Windows Defender functionalities? Provide them in the same order found.

9. Can you determine the URL of the second file downloaded by the attacker?

10. Identifying malicious tasks and understanding how they were used for persistence helps in fortifying defenses against future attacks. What’s the full name of the task created by the attacker to maintain persistence?

11. According to your analysis of the second malicious file, what is the MITRE ID of the tactic the file aims to achieve?

12. What’s the invoked PowerShell script used by the attacker for dumping credentials?

13. Understanding which credentials have been compromised is essential for assessing the extent of the data breach. What’s the name of the saved text file containing the dumped credentials?

14. Knowing the hosts targeted during the attacker’s reconnaissance phase, the security team can prioritize their remediation efforts on these specific hosts. What’s the name of the text file containing the discovered hosts?
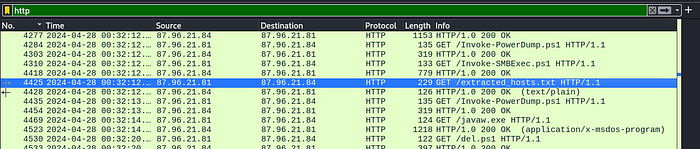
15. After hash dumping, the attacker attempted to deploy ransomware on the compromised host, spreading it to the rest of the network through previous lateral movement activities using SMB. You’re provided with the ransomware sample for further analysis. By performing behavioral analysis, what’s the name of the ransom note file?

16. In some cases, decryption tools are available for specific ransomware families. Identifying the family name can lead to a potential decryption solution. What’s the name of this ransomware family?


You Can Find me Here!
Last updated